Introduction
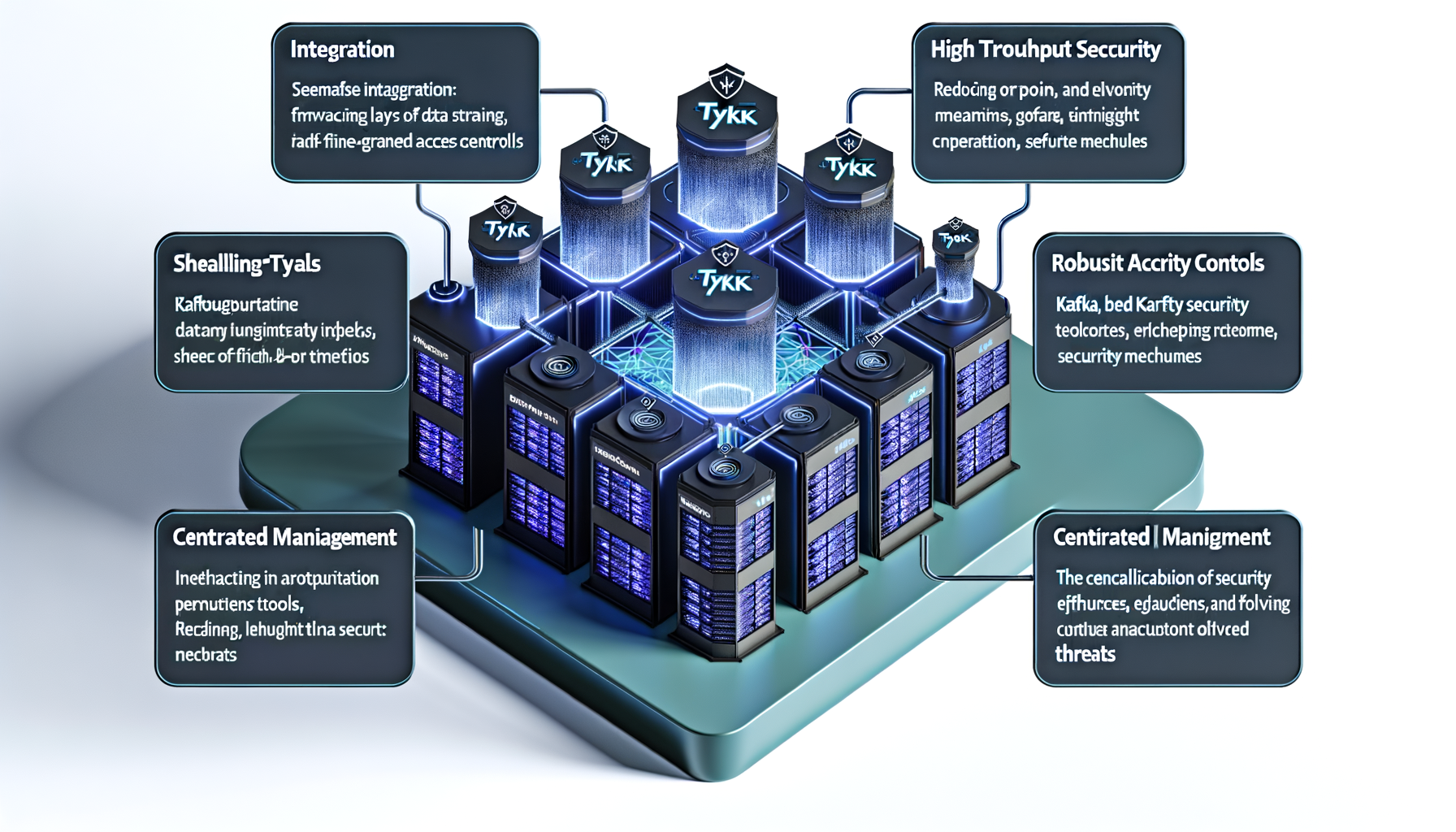
The article explores the integration of Kafka and Tyk Streams to enhance security and manageability in data streaming environments. Kafka, known for its high throughput and fault tolerance, requires robust security measures to protect sensitive data.
Challenges in Securing Kafka
Kafka’s architecture demands careful security configurations. Challenges include authentication, authorization, and encryption. Traditional methods struggle to offer an efficient, holistic approach, leading to vulnerabilities.
The Role of Tyk Streams
Tyk Streams emerges as a powerful solution to manage and centralize these security concerns over a Kafka-based infrastructure. It offers a layered security approach, ensuring end-to-end data protection.
Features of Tyk Streams
This platform provides tools for seamless integration, automated security policies, and fine-grained access controls. Tyk Streams ensures data integrity while maintaining high performance and throughput.
Benefits of Integration
By centralizing security efforts, it reduces complexity, mitigates risks, and enhances compliance with regulations. The integration allows for a unified security framework across various Kafka deployments.
Case Studies
Real-world applications show Tyk Streams’ effectiveness in diverse industries, demonstrating reductions in security incident rates and improved operational metrics.
Conclusion
Centralizing security using Tyk Streams significantly enhances Kafka environments, offering robust protection and streamlined operations. This holistic approach secures data effectively and efficiently, providing peace of mind for businesses.
Overall, adopting Tyk Streams for Kafka security not only simplifies management but also future-proofs the infrastructure against evolving threats.
View the original article here: https://tyk.io/blog/centralizing-kafka-security-with-tyk-streams-a-holistic-approach/