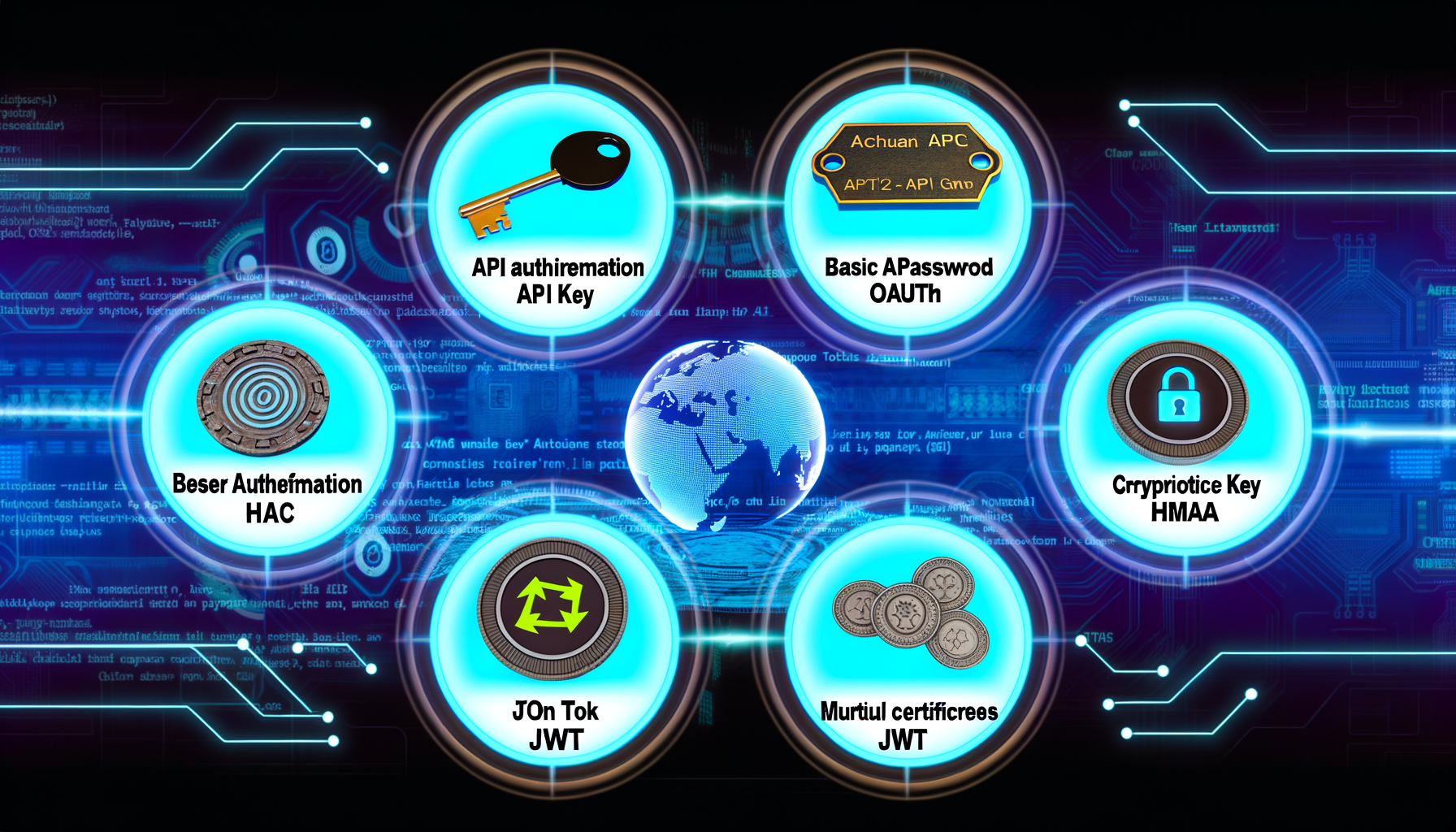
A Comprehensive Overview of API Authentication
API authentication plays a crucial role in securing data exchanges and protecting user data across various applications. In recent years, several methods have emerged as popular choices for enabling API authentication, each offering unique features and benefits. Understanding these methods helps in choosing the right one based on specific application needs.
Method 1: API Key Authentication
API Key Authentication involves validating requests by providing a unique key that is used to authenticate and authorize access. This method is relatively simple to implement and is beneficial for managing access controls effectively.
Method 2: Basic Authentication
Basic Authentication combines a username and password encoded in base64 format in the authentication header of the HTTP request. While easy to implement, it requires secure channels like HTTPS for transmission to ensure data protection.
Method 3: OAuth
OAuth is a widely adopted standard designed for token-based authentication and authorization. It is more complex but provides higher security and is especially useful for applications requiring user delegation or third-party access.
Method 4: Bearer Token Authentication
Bearer Token Authentication involves sending a token in the request headers to verify identity. It is straightforward and efficient, making it suitable for use in stateless applications.
Method 5: HMAC (Hash-based Message Authentication Code)
HMAC uses a secret cryptographic key to ensure that a message has not been tampered with. This method provides strong integrity checks but can be complex to implement correctly.
Method 6: JWT (JSON Web Tokens)
JWTs are a compact and self-contained way for securely transmitting information between parties as a JSON object. They are widely used due to their ability to include metadata.
Method 7: Mutual TLS (mTLS)
Mutual TLS requires both client and server to authenticate each other using certificates. This method provides a high level of security and is commonly used in enterprise environments where client validation is critical.
Conclusion
Selecting the appropriate API authentication method depends on various factors such as application requirements, security needs, and ease of implementation. By comparing these seven methods, developers can make informed decisions that ensure their applications remain secure while providing seamless access.
View the original article here: https://zuplo.com/blog/2025/01/03/top-7-api-authentication-methods-compared