Introduction
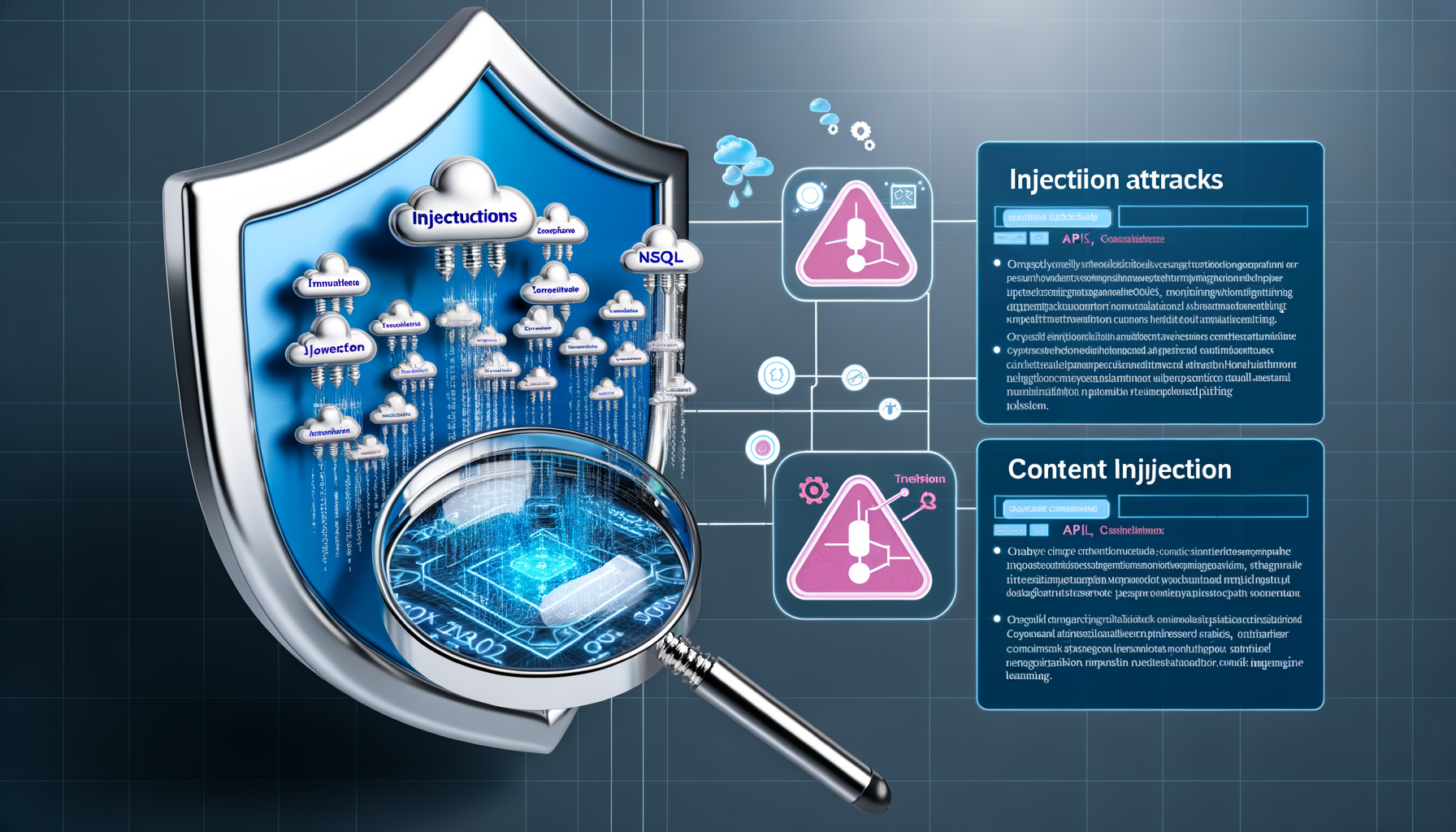
The article discusses the growing necessity of protecting APIs from injection attacks, which can compromise data and the integrity of systems. Injection attacks exploit vulnerable points in software systems, often targeting APIs, due to their critical role in data exchange.
The Threat of Injection Attacks
Injection attacks remain a potent threat due to the increasing integration and use of APIs. Attackers can use these vulnerabilities to execute arbitrary code or access sensitive information, causing significant damage to businesses and their clients. Common types of injection attacks include SQL, NoSQL, and command injections.
Content Inspection as a Mitigation Strategy
Content inspection involves examining incoming API requests to detect and block potentially harmful content. This approach can effectively mitigate the risks associated with injection attacks, ensuring only safe content is processed by the server. Such solutions integrate with existing API gateways, adding a layer of security without disrupting operations.
Features of Kong’s Solution
Kong introduces a new content inspection feature that leverages its adaptive security measures to protect APIs from injection threats. The feature utilizes pattern recognition, machine learning, and other cybersecurity techniques to identify and mitigate attack vectors in real-time. It boasts scalability and ease of integration with current API infrastructures.
Conclusion
With the rise in injection attacks, adopting advanced inspection methodologies is increasingly becoming a necessity. Kong’s content inspection feature provides a robust solution to secure APIs, offering enhanced protection against such threats. By implementing such measures, organizations can safeguard their data and uphold client trust.
View the original article here: https://konghq.com/blog/product-releases/content-inspection-injection-attack-protection